Have you ever wanted to task McAfee ePolicy Orchestrator (ePO) right
from Splunk? Lucky for us, ePO has robust Web API scripting capabilities and is
well-documented in a reference guide found here:
Combine this with Splunk’s flexible Workflow actions and we have the
basic building blocks to allow SOC analysts to task ePO. All that’s needed is
the following:
- Administrator access
to Splunk
- URL, port, and service
account (with administrator rights) to ePO
Testing the ePO API and credentials
In order to start the integration, let’s first ensure that our credentials, URL and port are correct. Using the curl command, we will send a few simple queries. If all is well, the command found below will result in a list of supported Web API commands.curl -v -k -u <User>:<Password> "https://<EPOServer>:<EPOPort>/remote/core.help
If this failed, then check your credentials, IP, port, and connection. Once the command works, try the following to search for a host or user:
curl -v -k -u <User>:<Password> "https://<EPOServer>:<EPOPort>/remote/system.find?searchText=<hostname/IP/MAC/User>
Pro Tips:
- Do not leave the
searchText parameter blank or it will return everything in ePO.
- Machine readable
output such as XML or JSON may be desired.
To return XML or JSON, use the :output parameter as shown in the
example below:
curl -v -k -u <User>:<Password> "https://<EPOServer>:<EPOPort>/remote/system.find?:output=json&searchText=<hostname/IP/MAC/User>
curl -v -k -u <User>:<Password> "https://<EPOServer>:<EPOPort>/remote/system.find?:output=json&searchText=<hostname/IP/MAC/User>
Our use case
There are many ways in which a SOC could benefit from Splunk/ePO integration. However, in this use case, we have ePO configured to perform automated actions (such as run a full AV scan) when certain tags are applied to hosts. Now wouldn’t it be convenient if we could tell Splunk to have ePO apply the tag to kick off the actions? How about clearing tags? Both actions are exposed through ePO’s API:Apply a tag: /remote/system.applyTag?names=<Host>&tagName=FullAVScan
Clear a tag: /remote/system.clearTag?names=<Host>&tagName=FullAVScan
Splunk Integration
One possible integration leverages Splunk’s Workflow Actions to issue these web API commands to ePO. This allows the analyst to pivot from the Event screen in a search using the Event Actions button as shown in the screenshot below: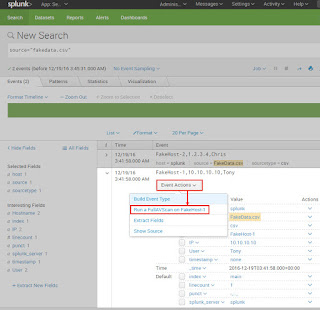
Splunk’s Workflow actions can be setup using the following:
Settings -> Fields -> Workflow Actions -> Add New
(Note: This example uses the field Hostname field to identify the asset, change this to match your field name):
Name: FullAVScan
Label: Run a FullAVScan on $Hostname$
Apply only to the following fields: Hostname
Apply only to the following event types: left blank
Show action in: Both
Action type: link
URI: https://<User>:<Password> @<EPOServer>:<EPOport>/remote/system.applyTag?names=$Hostname$&tagName=FullAVScan
Open link in: New window
Link method: get
Note: You may need to restart Splunk to make sure the Workflow Actions appear in the Event Actions drop down.
Security mitigations
This integration obviously exposes a lot of power to the Splunk analysts and potential attackers if Splunk is compromised. Here are some steps that can be taken to limit abuse:- Create a specific
service account in ePO for Splunk to use, do not reuse a user account
- Limit access to the
Workflow Action to a small group
- Set a Network IP filter
for the ePO/Splunk account to block any IP from using that account except
the Splunk search head
Results:
The results that are returned from ePO depend on the action performed, however the message seems consistent. See below for example messages for both a successful tasking and unsuccessful tasking.
Successful tasking:
|
OK:
1
|
Unsuccessful tasking:
|
OK:
0
|
Other possibilities
We have demonstrated the ability to query ePO for information by using
hostname, IP address, MAC address, and user.
We also showed how it is possible to apply and remove tags. But what else is possible? You could ask ePO using the first test
command used at the beginning of this article.
curl -v -k -u <User>:<Password>
"https://<EPOServer>:<EPOPort>/remote/core.help
|
OK:
ComputerMgmt.createCustomInstallPackageCmd
windowsPackage deployPath [ahId] [fallBackAhId]
[useCred] [domain] [username]
[password] [rememberDomainCredentials]
ComputerMgmt.create.Custom.Install.Package.Cmd.short-desc
agentmgmt.listAgentHandlers -
List all Agent Handlers
clienttask.export [productId]
[fileName] - Exports client tasks
clienttask.find [searchText]
- Finds client tasks
clienttask.importClientTask
importFileName – Imports
--snip--
|
To obtain help on a specific API command, but the following syntax with
the command parameter:
curl -v -k -u <User>:<Password>
"https://<EPOServer>:<EPOPort>/remote/core.help?command=core.listQueries
|
OK:
core.listQueries
Displays all queries that the
user is permitted to see. Returns the list of queries or throws on error.
Requires permission to use
queries.
|
Troubleshooting
If issues arise, just use the curl command to eliminate
complexity. Verify credentials, IP,
port, and connectivity, then move on to more complicated integration.
curl -v -k -u <User>:<Password>
"https://<EPOServer>:<EPOPort>/remote/core.help
Lingering concerns
Using this integration method, there are a few remaining concerns. There are:
- The ePO password is
contained in the Splunk Workflow setup screen
- Fortunately,
this is only exposed to Splunk admins.
- ePO API authentication
uses Base64. The resulting URL can
be modified and it will still be authenticated and will issue commands to
ePO.
- SSL in
ePO should be used to protect the data
- Leaving the
system.find searchText parameter blank returns everything in ePO
- ePO
seems resilient even to large queries
Conclusion
This is just one example of what can be done when integrating Splunk
and McAfee ePO. In our next article we will discuss further integration options
using a little python and simple XML. We hope this was useful if you are
ever tasked with integrating these two technologies.
Thank you, I appreciate the feedback.
ReplyDelete